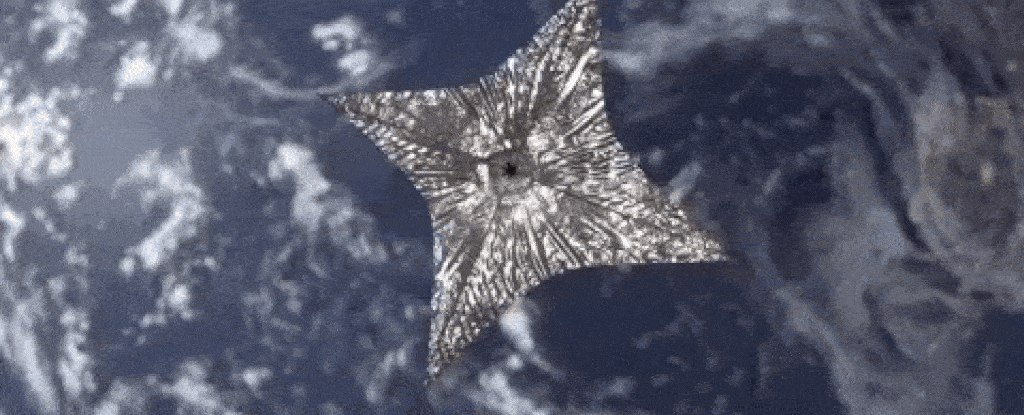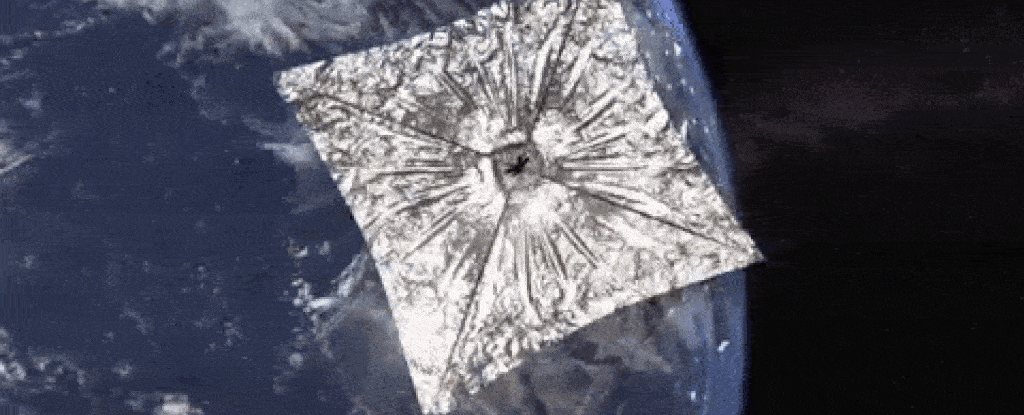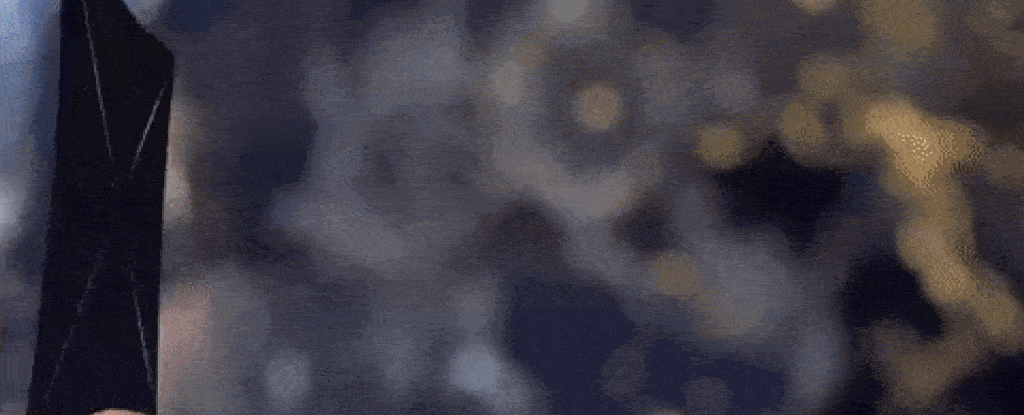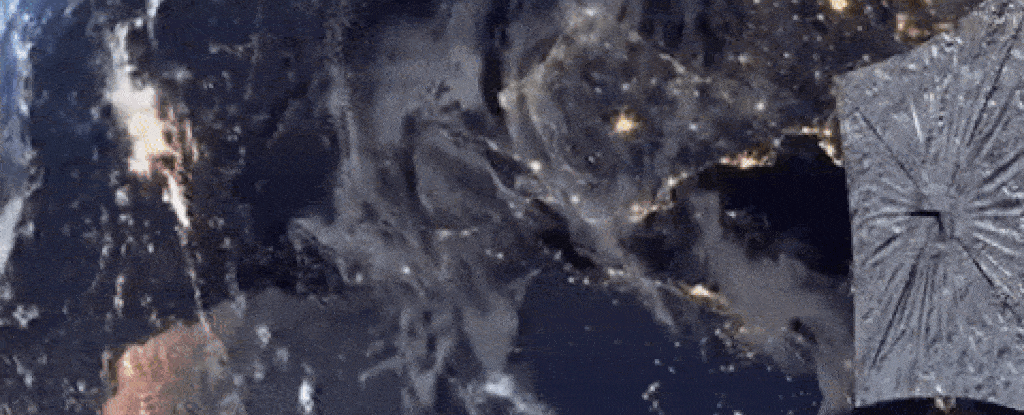
My impression is that there isn't much distinction between what is contracted to companies and what is done in house. It's a big world but at the same time a small one.
Going back to the leaks Snowden (himself working for a contractor) released, there's a lot of cooperation going on.
Do you know what Solarwinds actually sells? Have you ever purchased anything from them?